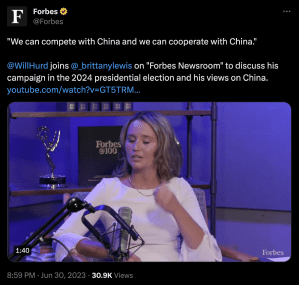
The Internet is full of threats that could harm your computers, mobile devices, tablets, or other connected products. It’s important to understand how these threats work so you can keep yourself safe online, prevent data breaches and be protected from a cyber attack.
The Current State of Cybersecurity and the Consumer
Two years ago, Americans lost $4.5 billion because of cybercrime. Two years from now the amount of money lost is expected to be $10.5 trillion.
Unfortunately, we all must take an active role in protecting ourselves, our households, and our places of work. We can’t just leave cybersecurity up to the cyber security professionals at our employers or cyber security specialists who work at the companies whose applications and software we use.
Cybersecurity is complicated but everyone can do it. Let’s begin our 10 things we need to know to protect ourselves with something simple.
1. Cybersecurity and cyber security are the same thing.
One of the first questions I often get asked is whether cybersecurity is one word or two? I follow what many in the cybersecurity community in America do and spell it as one word with the exception being when using it as an adjective to designate a certain kind of security out of many options.
Whether it’s spelled as one word or two, the definition and concepts remain the same. The best cybersecurity definition in my opinion is as follows:
- Cybersecurity is the branch of information security that helps protect data and information in our digital systems from a cyber attack.
This leads into the second most asked question I get, what is a cyber attack?
- A cyber attack is any type of unauthorized or malicious activity that takes place over a computer network. Cyber attacks can take many forms, but some common examples include:
- Distributed denial of service (DDoS) attacks, which aim to make a website or server inaccessible by flooding it with traffic.
- Ransomware attacks, in which malware encrypts a victim’s files and the victim must pay a ransom to get access to the encrypted files.
- Phishing attacks, in which fraudulent messages are used to trick someone into giving away sensitive information like passwords or credit card numbers.
- Intrusion attacks, in which a hacker gains unauthorized access to a system and may steal, damage, or alter data.
2. In cybersecurity, data is the coin of the realm.

Source: Finances Online
Current events in cybersecurity have made data become extremely valuable in today’s world increasing the threat of identity theft. Attackers are evolving their practices from gaining control of computer systems or devices to gaining access to sensitive data like your user credentials or account information.
This sensitive data can also include personally identifiable information (PII), health information, private communications, customer data and intellectual property.
- Personally identifiable information (PII) refers to any data that can be used to identify a specific individual. This type of information is often targeted by hackers or scammers in order to exploit or steal someone’s identity. PII can include things like name, address, date of birth, social security number, or credit card number.
A user’s identity or credentials are becoming more valuable to attackers than gaining technical access to a user’s device, making data theft an increasing threat and data security even more important. The first and most important step in data security is password protection – have a unique 14-character-plus password for each site requiring a password.
3. Phishing attacks start more than 90% of successful cyber attacks.

Screenshot of an actual phishing text message
So, think before you click. Typically, phishing attacks will involve a scammer sending an email or text message that looks like it is from a reputable company or organization, in order to trick the target into revealing sensitive data like passwords or PII that is then used by the attackers to conduct data breaches.
Once bad guys have this information, they can use it on legitimate sites, or they may try to get you to run malware.
- Malware is a type of malicious software designed to gain access to a computer system without the owner’s knowledge and permission. It can take many forms, including viruses, worms, ransomware, and spyware.
If you get an email you don’t expect or from a user you don’t recognize, trust your instincts – don’t open it and think before you click on links. The Cybersecurity & Infrastructure Security Agency (CISA) has some good tips on phishing prevention.
4. More than half of cyber attacks and data breaches could be prevented with up-to-date software on your devices.

Microsoft Windows display showing patches are available
If you or your employer do not have the proper security infrastructure and practices in place, cybercriminals will easily target you. According to a study conducted in 2018, an alarming 57% of cyberattack victims report that their breaches could have been prevented by installing an available patch, and 34% of those respondents were already aware of the vulnerability before they were attacked.
- Patching is the process of updating computer software to fix security vulnerabilities and improve the overall performance of the system. It involves installing patches, which are small pieces of code, to address security flaws, improve system stability, and add new features.
Patching is important for keeping systems secure and up to date, as security vulnerabilities can be exploited by malicious actors. So make sure you have ways of keeping up to date important types of software like:
- web browser
- third-party apps
- antivirus software
- operating system (OS)
Most OS’s – Windows, Apple, LINUX – support automatic updates but this feature needs to be enabled. But to stay safe in this increasingly digital world, a consumer needs to have their own plan for patching promptly to protect themself.
5. Malvertising can lead to ransomware attacks.

Malicious advertisement promoting a fake Chess app, Source: Bleeping Computer
Advertisements, like the above ad for a fake Chess app, are a prime example of malvertising. When a user clicks on the ad, they are then taken to a fake Microsoft Store page (see image below) for a fake online chess application, which is automatically downloaded from one of the legitimate cloud services used by the attacker.

Fake Microsoft Store page distributing the Ficker malware, Source: Bleeping Computer
The downloaded file is not a Chess app but information-stealing malware in disguise. Malvertising is a particularly effective method of spreading ransomware, as it allows cyber criminals to target large numbers of users quickly and without their knowledge.
- Malvertising stands for malicious advertising and is a type of online advertising that uses malicious code to spread malware or deploy ransomware. Malvertising involves the use of malicious code embedded in legitimate online advertisements, which once clicked redirect users to malicious sites or download malicious files without the user’s knowledge.
Malvertising is used to install ransomware by exploiting weaknesses in web browsers, such as outdated plugins or software. The quickest way to avoid being a target of malvertising is to enable ad blocking in your web browser, but this also limits your ability to see legitimate ads.
Malvertising is a particularly dangerous form of ransomware attack, as it can spread quickly and without the user’s knowledge.
Malvertising, phishing and social engineering is how ransomware spreads. Last year was the worst year for ransomware attacks statistically and information security analysts believe 2023 is expected to be worse.
To protect against ransomware, you must do some of the same things to prevent against other attacks. However having data duplication where your most important data is backed up and you know how to recover it is advised. This is getting easier to do with the number of cloud services available to consumers and the improvement of cloud security by these providers.
Future Cybersecurity Threats Consumers are Facing

Notorious hacker Marcel Lazar Lehel AKA Guccifer after his arrest in Romania in 2014, Source: Reuters
Cyber theft is already a major problem and it’s only getting worse. Cybercriminals are constantly changing the ways they target businesses, steal from individuals and attack security systems.
The rapid pace of technological change has created opportunities for cyber criminals to exploit new vulnerabilities, and many organizations are struggling to keep up. The most vulnerable sectors tend to be those that rely on legacy systems, lack robust network security or are unprepared for the latest cyber threats.
6. The future of cybersecurity is good AI versus bad AI.

HAL 9000 from the 1968 film 2001: A Space Odyssey
Artificial Intelligence (AI) can be used in many different areas such as robotics, image recognition, natural language processing, and automated decision making.
- Artificial intelligence (AI) is the ability of a computer or a machine to think, reason, and learn.
AI is an area of computer science that focuses on the development of algorithms and systems that can learn from data, recognize patterns, and make decisions with minimal human intervention.
Cyber criminals may use AI to automate cyber attacks and make them more difficult to detect. For example, they may use AI to generate malicious code that can bypass traditional security measures, launch sophisticated phishing campaigns, or brute force break into systems.
AI can also be used to detect vulnerabilities in systems and launch targeted attacks. Additionally, AI can be used to analyze large amounts of data to identify patterns and discover new attack vectors.
7. Quantum supremacy will transform cybersecurity by breaking all current encryption protocols.

IBM’s Osprey Quantum Computer. Source: IBM
Quantum computers will be able to solve problems in seconds that today would take traditional computers thousands of years.
Instead of bits that are either 1 or 0 (on or off), quantum computers use qubits that can be in a state called superposition.
- Superposition is a state where qubits are both on and off at the same time, or somewhere on a spectrum between the two.
Quantum computers will also be able to do a thing called entanglement.
- Entanglement is the linking together of two particles, even if they’re physically separate.
This might sound like magic but managing superposition and entanglement will allow us to build better batteries, reduce traffic in our cities, design new cures for deadly diseases or break all the encryption that is used today to protect sensitive data.
If the world fails to deploy quantum-resistant encryption the impacts to communications systems, financial information and government secrets could be catastrophic, leading to a loss of privacy and security breaches on a global scale.
8. Our surface area of attack is growing because of the Internet-of-Things.

Examples of “Smart,” connected devices, Source: The Ambient
As our world becomes increasingly interconnected, the risks to our personal data and digital lives continue to grow as we rely on technology for everything from online shopping to controlling our home appliances and other connected devices through the Internet-of-Things.
- The Internet of Things (IoT) refers to the interconnection of physical devices, systems, and services via the internet.
The more devices we have that are connected to the Internet the greater our digital footprint becomes. A larger digital footprint means more things for cybercriminals to attack.
While IoT has the potential to bring many benefits to our lives, it also comes with several cybersecurity risks like:
- Lack of security by design – Many IoT devices are designed without built-in or network security measures, meaning they are vulnerable to hacking.
- Data leakage – Many IoT devices collect and store data, which can include sensitive information such as health records or financial data. If this data is not properly secured, it could be accessed by unauthorized individuals.
- Botnets – IoT devices are an attractive target for botnet operators, who can use them to carry out nefarious activities like DDoS attacks, which is like a giant flood of data that can take down a website or network. A botnet is a network of computers used by cyber criminals to send this massive amount of data that overloads the server or network, making it too slow or even completely unavailable.
- Lack of regulation – Currently, there are few regulations or standards specifically for IoT security, which means that manufacturers are not held accountable for the security of their devices. This has led to a “wild west” environment where security is often an afterthought.
9. Critical Infrastructure security will be increasingly at risk, causing digital attacks to have more impact on the physical world.

The Bruce T. Haddock Water Treatment Plant in Oldsmar, Florida, Source: Chris Urso, Tampa Bay Times
Critical infrastructure, such as water systems, energy companies, electrical grids, and transportation networks, are increasingly becoming targets of cyber attacks. In the past few years, there have been numerous cyber attacks highlighting the vulnerability of critical infrastructure, including:
- The NotPetya computer virus spread across the computer networks of more than 60 countries in June 2017. This Russia cyber attack, specifically conducted by the Russian military, exploited a vulnerability in the Microsoft Windows operating system to cause an estimated $10 billion in disruption and destruction to banks, airports, power plants, transportation companies and governments.
- The Oldsmar, Florida Water Treatment Plant cyber breach took place in February 2021 when a hacker using stolen credentials gained remote access to the city’s water treatment plant and attempted to poison the city’s water supply by increasing the chemicals in the water to a deadly level.
- The Colonial Pipeline ransomware attack in May 2021 resulted in the shutdown of the largest fuel pipeline in the United States, which delivers 45 percent of the fuel for the East Coast. The attack was not carried out by a nation state to disrupt the economy but by a criminal group to hold corporate data for ransom. It had a significant impact on fuel supply and prices.
Consumers should be concerned about these attacks because they can have a significant impact on the availability and reliability of essential digital services AND physical services as well. The Oldsmar Water Treatment Plant cyber attack is an example of how terrorists could resort to cyberterrorism to achieve their aims.
Taking Measures to Reducing the Severity, Seriousness, and Painfulness of Cyber Attacks
As we enter the new year, ransomware infection is becoming more prevalent, and phishing scams are becoming more sophisticated. There is also the growing threat of cyber warfare and state-sponsored attacks from Russian and China, which could target critical infrastructure. Individuals can only do so much to protect themselves from cyber attacks. Businesses, industries and governments need to do more to create a better environment for consumers to live their digital lives.
10. Standardize cybersecurity protocols across industries.

Future home of CISA, Source: Department of Homeland Security
As one of the newest federal agencies, established in 2018 CISA has been leading a national effort to protect the nation’s critical infrastructure from physical and cyber threats. Companies and other cybersecurity leaders are working to secure consumer data by implementing stronger security measures and educating users on best practices.
There is an opportunity for standardization in cybersecurity policies and protocols through joint efforts from industry and government.
- Cybersecurity policies and protocols are plans, rules, actions, and measures to use to ensure your company’s protection against any breach, attack, or incident that may occur. Data has become some companies most valuable assets, so ensuring the protection of your data has become more vital than it ever has been.
Standardized cybersecurity protocols would allow for a common set of best practices to be shared across different sectors and could help reduce the number of attacks. Something as simple as coordinating cybersecurity polices and protocols is one way America will improve its cybersecurity.
11. Hit our enemies, establish norms with our friends, pressure everyone else.

Canals of Bruges, Belgium: According to UNCTAD, Belgium doesn’t have a cybercrime legislation
Over the years cybersecurity policy of the United States has failed to do three things:
- Encourage all governments to adopt laws making cyber attacks illegal or constraining the ability of cyber criminals to operate within all jurisdictions.
- Convince adversarial governments to accept norms around cybersecurity and cyber war.
- Impose sufficient costs on attackers to make them think twice before perpetuating an attack.
Nation-states need to be held accountable for malicious cyber activity emanating from their territory. This is the only way they will develop the legal and technical capabilities to improve poor cyber security procedures making the rest of the world more vulnerable.
Norms are more useful in binding friends together than in constraining adversaries. The United States should work with allies to agree on norms necessary to prevent catastrophic outcomes like destructive cyber attacks on election and financial systems. We should also develop joint practices for handling zero-day vulnerabilities (flaws in software not known to the public) and improve transparency between allies about cyber operations.
Cyber criminals need to think twice before they execute an attack. The only way this happens is if they think the consequences of their actions are going to be greater than whatever booty they gain. When responding to cyber attacks the US government and our allies have to be willing to use more than just digital tools to respond. We should be prepared to make the digital infrastructure used in the attacks inoperable and use tools in the physical world like sanctions, arrests and seizure of assets.
12. Achieve good digital hygiene.

We relearned a lot about personal hygiene during the pandemic. To reduce our chances of getting COVID-19—wash hands, wear a face mask, and practice social distancing. For our online lives, there is digital hygiene.
Good digital hygiene is all about having a personal cyber security risk management plan that makes sure you are deploying best practices to keep yourself safe online. The basics of good digital hygiene or a personal cyber security risk management plan have four elements:
- Password Protection – have a unique fourteen-character-plus password for every system that requires a password.
- Patch Promptly – keep your software on your phone or laptop up to date in order to protect your devices against a vulnerability discovered by the company that wrote the software.
- Phishing Prevention – resist clicking on attachments in your email or texts from someone you don’t know.
- Data Duplication – establish a data backup and recovery plan for your most important data to be prepared in the event of a ransomware infection.
Just like good personal hygiene can prevent you from getting sick. Good digital hygiene helps to ensure the security and privacy of your digital information and data.
Bottom-line
Cybersecurity is important because it is necessary for us to have a safe, productive, and fun digital life. The current state of cybersecurity is one of constant vigilance. Cyber security threats to consumers continue to evolve but following the 6Ps and 2Ds of digital hygiene will protect you from a majority of cybersecurity threats.
First time reading? If you want rational takes on foreign policy, politics and technology then sign up below or click here for “The Brief.” It’s a twice-a-month email on things that aren’t being discussed but should – all in 5 minutes or less.